What is 3Access
It is becoming more overriding the need to control and manage the movement of people and / or vehicles that enter and exit certain facilities. A Management and Access Control System is in charge of enable users for admission to various areas, establishing groups of permissions that define the degrees of restriction that each user has.
A door is a very basic way to control access, and brings complications at the time that keys is lost (or stolen) without being no record of users which raffled it.
So was born 3Access, a system of access control, which allows the configuration of rights of access and its management and compliance through different step control devices adaptable to the needs of the campus.
3Access architecture
Access Methods pedestrian and vehicular
3Access establishes groups of permissions that define people in terms of level of accessibility, ie as access to which each user is enabled and the timetable (days, times, etc.) for the application of permits.
This requires the user to hold a key to unlock access barriers and allow its passage. This access control system offers different methods as required for each installation, focused on its pedestrian use and / or vehicle.
The fact that the 3Access perform management and access control system does not rule out the need for security personnel, who can detect alarm conditions generated by the system and act accordingly.
Mobile app
Pedestrian / Vehicular
The user installs in the mobile a specific app, with which will identify and access the facility.
RFID card
Pedestrian / Vehicular
A proximity card, previously delivered to the user, which allows to unlock the door closer approximating it near the RFID reader.
MIFARE card
Pedestrian / Vehicular
MIFARE is a special type of proximity card, and works at the same way as an RFID card.
Intercom
Pedestrian / Vehicular
Installing an intercom access, the user can communicate with the control point, which will unlock the door.
Digital fingerprint
Pedestrian
The user places his finger on the fingerprint reader installed on the door and unlocked it if detects that the fingerprint is registered in the system.
License plate
Vehicular
The bollards, installed in the road of a vehicular access, will read vehicle license plate, opening the barrier if it has permission to access.
Long range TAG
Vehicular
A remote antenna recognize the TAG device placed in the customer’s vehicle and opening the barrier.
Wireless TAG
Vehicular
Works just like a long-range Tag, but with BLE technology.
Access elements Control doors
The access control system has different obstacles to enter and leave a facility. All of them are connected to the system, allowing to monitor their status, any irregularities, etc.
Turnstile
We have different turnsitle depending on the installation, with a range spanning from compact and economical ones with great security, with folding blades to variable height turnstile.

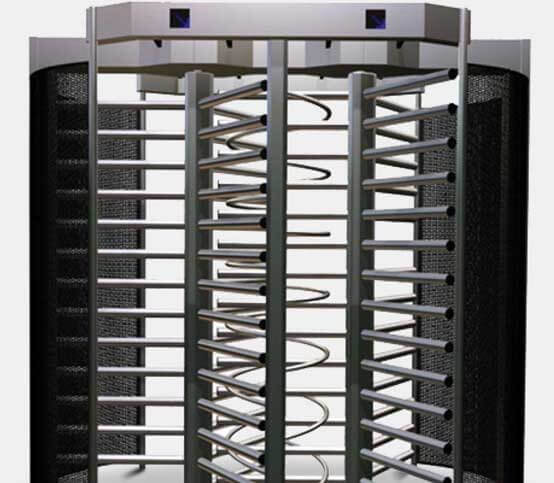
Full-Height Turnstile
3Access offers three row full-height turnstiles for facilities that require a high degree of safety and high mechanical strength. We offer double full height-turnstile for installations where space is limited.
Automatic wicket gate
Different motorized access wickets designed to channel the people flow, shopping areas and commercial establishments. There are unidirectional, bidirectional, for disabled persons and optical gateways models.

Vehicular access
We have barriers, TAG readers, license plate readers, among others, for access control to vehicles.

Software access control
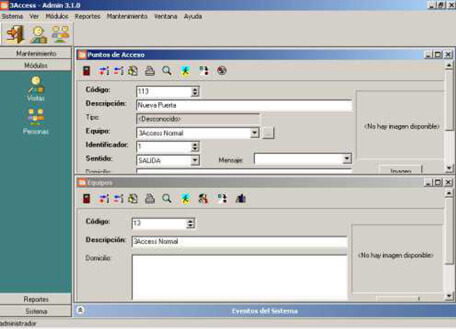
3access system is a powerful software designed to carry out the administration and access control, focused on the simplicity of operation for the user and in a wide range of functionalities.
Interface
From 3Access software the system admin can control users and their permissions, to register new people, linking access methods and be informed of the possible events and incidents that may arise.
People
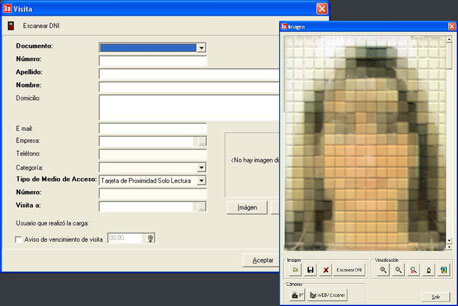
The software allows full control of the people who will access the facilities.
Through it you can deregister, register or modify the data of a person, and later assign an access method and establish a temporary (allow access to certain hours or days.)
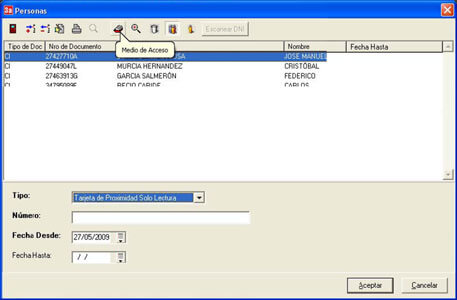
Access means
Control all access means to the facility and associate one to a particular person who has been registered previously in the system.
In addition, you can introduce an expiration date to it.
[printfriendly]
